Cloud Migration
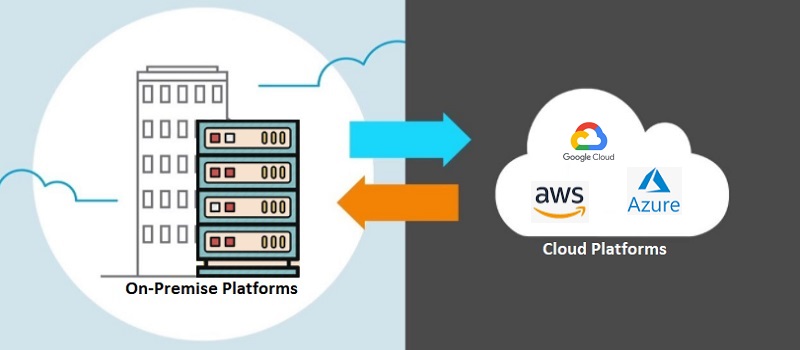
With Cloud Migration being at the forefront of Federal IT system modernization efforts, we offer clients our years' of experience performing Cloud Migrations on high-volume transaction processing systems for both public and private sector clients.
Our company leaders, architects and engineers are adept at creating pragmatic Cloud Migration roadmaps that consider client's technical and business requirements such cost, security, scale and timeline.
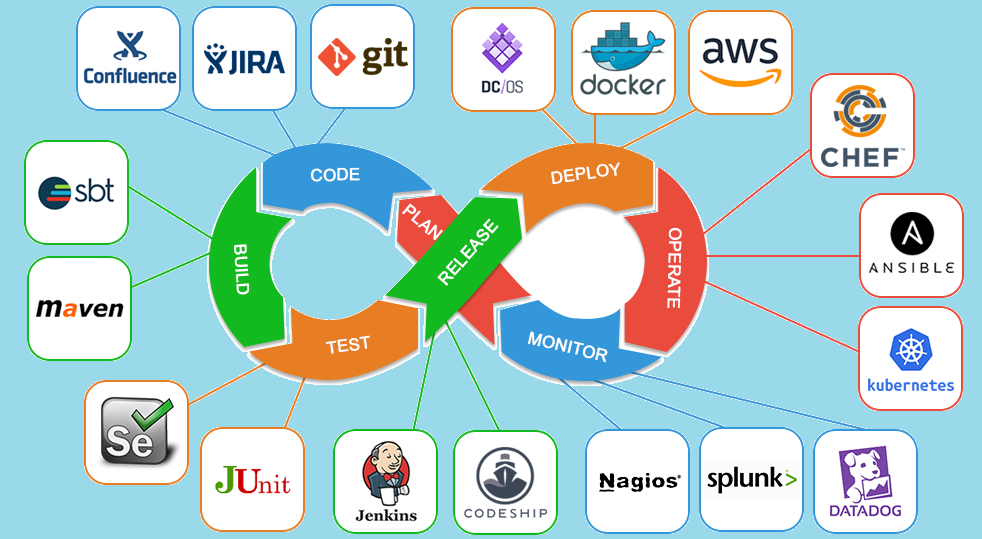
Our engineers have re-architected legacy systems by decomposing workloads into containerized functional microservices that can be independentaly updated, scaled and deployed.
Our technology experience includes developing any cloud agnostic application using Docker, Docker Swarm, Kubernetes (Konvoy) for AWS, Azure and Google Cloud.